


Companies may want to use their software forever, but every system has its limits. Unlike some things that last indefinitely, software and applications installed on workstations eventually become outdated. The end can come sooner than expected, so it’s important to be prepared. This blog highlights the risks of using outdated software and provides a plan for smooth modernization.
In the past, major software updates, like new Windows versions, were released every five to six years. Upgrading was optional unless new features or support were needed.
However, with the rise of the Internet, regular software updates have become essential. Increased online connectivity exposes systems to serious threats like viruses, malware, scams, and hackers.
A report on the NHS cyberattack revealed that outdated software was one of the main reasons for the breach. When Microsoft releases updates, they do more than introduce changes—they also work to improve security and protect your system.
Yet, no software development company can support a product forever. After a set period, a program reaches its “end of life” (EOL), meaning it will no longer receive updates or bug fixes.
When we inform clients that their software has reached EOL and needs an upgrade, they often ask:
In this article, we will answer these questions and explain why outdated software requires immediate attention.
End-of-life (EOL) software refers to the software that no longer receive updates or support from the vendor. This means no new security patches or bug fixes will be released. Using EOL software can be risky because it becomes more vulnerable to cyberattacks and may be harder to maintain due to a lack of support or documentation.
Companies usually announce EOL dates in advance, allowing users to prepare. It is important for both users and businesses to stay informed about these updates and take necessary steps, such as upgrading to the latest version, switching to an alternative, or adjusting their systems. Understanding EOL software helps ensure digital tools remain secure and functional in a constantly evolving tech environment.
Our digital world keeps changing, and software products eventually reach their end of life. This means they no longer receive updates or support, making them less secure and outdated. Here are some well-known software products that have reached their end:
If you’re thinking about saving money by using outdated (EOL) software beyond its lifespan, you might want to reconsider. While it may seem like a cost-effective solution, this choice comes with serious risks:
EOL software no longer receives updates, bug fixes, or security patches, making it vulnerable to cyber threats. If a security flaw appears, vendors won’t provide fixes, leaving your system exposed. This not only puts the outdated software at risk but also threatens your entire network.
Using outdated software can lead to data breaches, putting sensitive business and personal information at risk. Regulations like the General Data Protection Regulation (GDPR) impose heavy fines on companies that fail to protect user data. Ignoring software updates increases the chance of legal penalties and financial losses.
Old software often doesn’t work with modern applications and operating systems. For example, an outdated system like Windows XP may not support new apps, causing disruptions. Running incompatible software can slow down performance, increase crashes, and create unnecessary technical issues.
Legacy software tends to run slowly and is less reliable. Older systems are more prone to breakdowns, leading to frequent downtime. Instead of dealing with sluggish performance and unexpected failures, upgrading to newer software can save time and improve efficiency.
Sticking with outdated software may seem like a budget-friendly decision, but the long-term costs of security breaches and system failures can be much higher. Investing in modern software solutions, including cloud-based services like Salesforce or Mailchimp, can be more cost-effective in the long run.
Employees expect to work with up-to-date technology. Using outdated systems can frustrate them and reduce productivity. In today’s workplace, where many companies adopt Bring Your Own Device (BYOD) policies, staying current with technology is essential to keep your workforce motivated.
Upgrading your software isn’t just about keeping up with trends—it’s a critical step to protect your business, ensure compliance, and improve efficiency.
As per the reports from Gartner, 30% of critical infrastructure organizations will experience a security breach by 2025.
Software changes over time, and it’s important to know when it is reaching its “end of life” (EOL). EOL means the manufacturer will no longer provide updates or support. Signs of this include no recent updates, bug fixes, or security patches. You can also check the software company’s website or official announcements for the EOL date.
Paying attention to these updates is essential because using outdated software can lead to security risks and compatibility problems. Newer software versions may also have better features and support. To keep your system secure and up to date, watch for these signs and check the manufacturer’s official sources for EOL details.
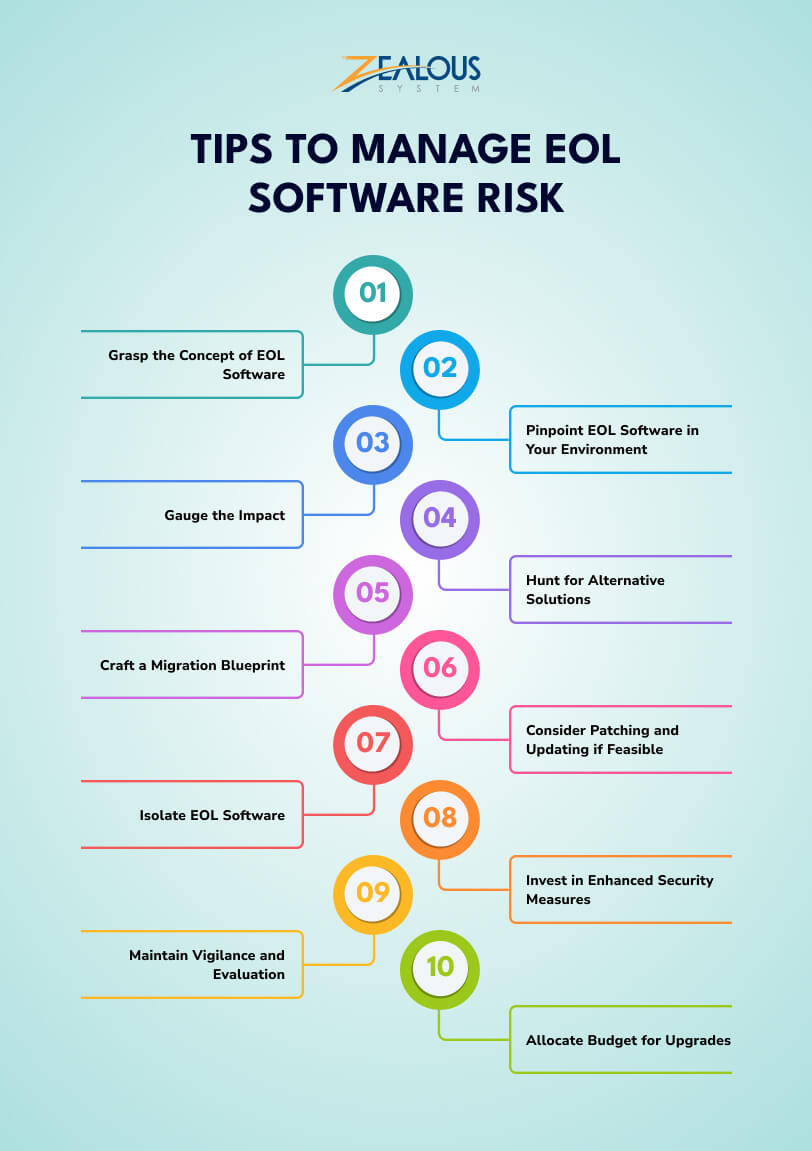
Managing EOL software properly is crucial to keeping your systems secure and efficient. Here are the best practices to reduce risks and ensure a smooth transition.
EOL software no longer receives updates, bug fixes, or security patches from the manufacturer. This makes it vulnerable to security threats and compatibility issues. Understanding this concept helps in making informed decisions.
Regularly check your software inventory to spot applications approaching or already at EOL. Look for vendor or dedicated developer announcements, lack of updates, or notifications about discontinued support.
Analyze how the EOL software affects your business. Consider security risks, performance issues, and potential compliance violations. Prioritize software that is critical to operations.
Explore modern alternatives that offer better security, features, and support. Compare different options based on cost, ease of migration, and long-term benefits.
Plan a smooth transition to new software by outlining necessary steps, timelines, and resources. Involve key stakeholders to minimize disruptions.
If replacing the software immediately isn’t feasible, check if unofficial patches, extended support, or temporary fixes are available. This can help reduce risks while you prepare for migration.
If you must continue using EOL software, limit its access to critical systems and networks. Use firewalls, virtual machines, or other containment strategies to reduce potential threats.
Enhance security by using antivirus programs, intrusion detection systems, and strict access controls. Regularly monitor for unusual activity to prevent breaches.
Keep track of all software in use and regularly review your IT environment. Stay updated on upcoming EOL dates and plan ahead to avoid last-minute risks.
Allocate funds for software upgrades and replacements. Planning a budget in advance ensures you can transition smoothly without financial strain.
By following these best practices, you can effectively manage EOL software risks and keep your systems secure, efficient, and up to date.
In short, knowing about end-of-life software is important in today’s fast-moving digital world. We’ve covered what it means, looked at some real examples, and talked about the risks involved. But don’t worry—there’s a positive side to it!
By staying updated, going with an experienced custom software development company, and planning ahead, we can smoothly handle the challenges posed by aging software. As we wrap up, remember that knowledge and proactive measures empower us to make the most of our technology and maintain a great digital experience.
Our team is always eager to know what you are looking for. Drop them a Hi!
Comments